How to Clean Ripped Landing Page
One of the most common tactics affiliates use to get landing pages for their campaigns is using a spy tool to download other affiliate's landing pages and use them as their own.
Lazy affiliates will just make the landing page function, make no additional changes/additions and call it a day.
Smart affiliates on the other hand will modify the lander they download and improve it so it converts better than the page they downloaded.
Either way, ripping landing pages requires a bit of skill to not only make the page function correctly but also remove any malicious scripts that could steal a percentage of traffic that goes to that page.
Today I'm going to show you some basic steps you should take to clean ripped landing pages after you download them.
As noted in my free method to finding CPA affiliate landing pages to rip without a spy tool, you should have basic knowledge of HTML, CSS and Javascript to do this correctly.
Check the Files You Downloaded
What files were downloaded to your computer when you ripped the landing page? Check what files you have.
Identify what page is the index.html and also any other potential files that could cause problems (CSS, JS, PHP, etc.).
This should always be the first step when cleaning up ripped landing pages.
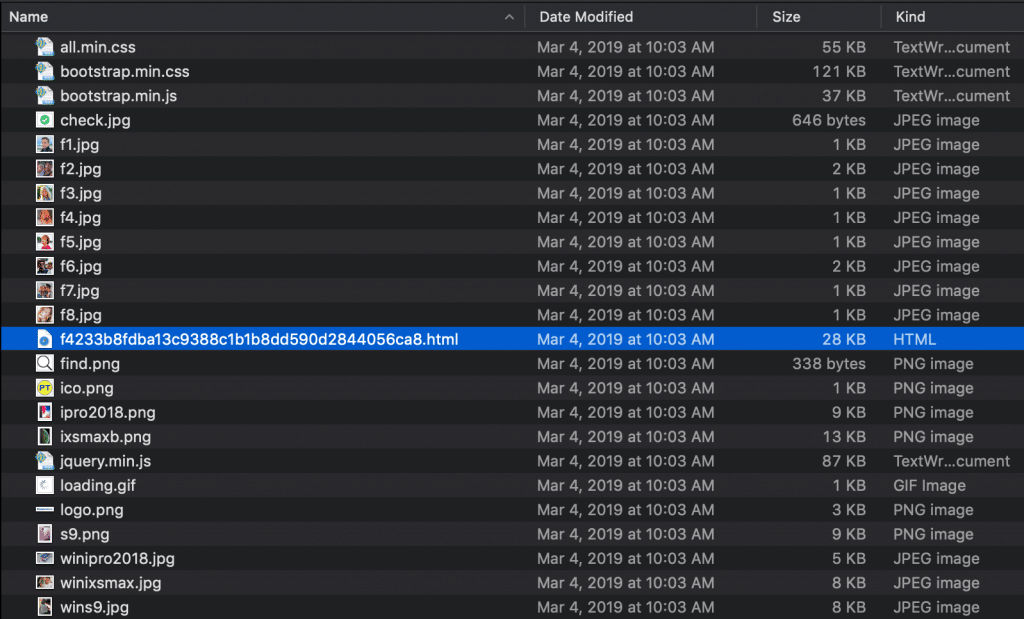
In the image above, the highlighted file should be the index.html page. I always rename this right away so I don't get confused.
Other potential problem files that we know we are going to have to check/replace are:
- all.min.css
- bootstrap.min.css
- bootstrap.min.js
- jquery.min.js
How do we know we are going to have to check or replace the above files? Malicious scripts could be hiding in them.
Usually, at this point, we want to open the index.html file in our browser. Does it look like the page we meant to download? If yes, we start cleaning the page up for our use.
Look For Links to External Files
Under no circumstances do you want to leave links to external websites (not counting official CDNs) in your landing page. All it takes is the website owner to change that link, for example, an image, from an iPhone to porn for your campaign to completely tank.
In a code editing program, search for http://, https:// and //. This should lead to any outbound links.

Don't forget to do this for CSS and JS files, as outbound links can be hidden in those as well.
If there are images hosted on another domain than yours, visit those links in your browser and download them and add them to the folder your index.html is in.
During this process you will likely find the tracking links of the affiliate you downloaded the page from. Replace these links with your own.
Replace Problem Files
Remember those four problem files we identified when we checked the files we downloaded? Let's replace them (I usually will replace them instead of checking them to save time).
The Bootstrap CSS and JS files can be replaced from the official BootstrapCDN website. Just replace the direct file links in your index.html with the CDN links.
The Jquery file can be replaced with a link from the official CDNjs website.
Some affiliates recommend that you should use files hosted in Google's Library, as there is a good chance the visitor may already have the file cached when they load your landing page, leading to slightly faster loading time.
I don't like to do this because I'm paranoid. I've read in the past that there is a callback to Google's servers when those files are loaded, which could lead to other problems we won't discuss here.
The last file we have that we identified at the start was all.min.css. Because this is just a basic CSS file, we should see if we even need it.
Comment it out in the HTML code like this:
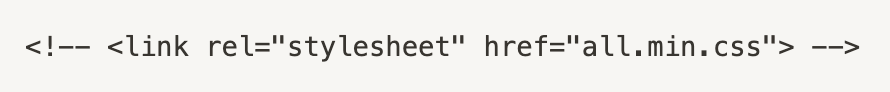
Notice the characters at the start and end of the line? This makes the browser ignore the code. Reload the page and in your browser and see if it still works.
In this case our page still works because this CSS code is also between style tags in our HTML.
If we actually needed this file, we'd have to check for external links and Javascript within the file and remove/replace it. I also like to put all the CSS styles in style> tags within the head of the HTML for faster loading time.
Search and Audit .js in Index.html
In this particular example, we replaced the Javascript that wasn't within the index.html file. Now, there are still some scripts in the index.html.
To find these, we can search for script.
You have to look at each script in the page and identify what they are supposed to do. I'm no Javascript expert, but the way I like to do it is figure out the general purpose of the script and if it's coded differently than the scripts I usually use, I'll replace it with my own script.
If there is a script I have no idea what it does, I'll comment it out as shown above and reload the page and see if it still works. Refresh the page in your browser, and if it still works without the script, you can simply delete it.
If your page contains Javascript that inserts content into your page (dates, days of the week, url paramters, etc.), you have to delete the content.
Every Thursday we randomly...
When you don't do this, you might have your page load with something like this: "Every MondayThursday we randomly...". You'd be surprised how many people forget to do this and run the campaign anyway.
Find Base64 Code
Base64 is a type of encoding. It can look rather weird when you find it in a landing page:
data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABEAAAAQBAMAAAACH4lsAAAAJFBMVEX///87WZhPaqNac6hieq12i7d6jrmRosWfrsy2wdjEzeD///+4DpBBAAAAAXRSTlMAQObYZgAAAD5JREFUCJljYMAFhGAMlk0wFuNGGKsVzpLeKJgApBwFBXfv3i0AZIkX7oayRAPxswSjdu82AOtlmCoojN0VACVEF76WXuvhAAAAAElFTkSuQmCCThe above encoded string is an image. The most common use is for images, but I've heard Javascript can also be hidden like this. So if you don't think it's actually an image you're going to want to find out what it does.
This tool can be used to decode the image and see what it is and this tool can decode normal text.
Deobfuscate Suspicious Javascript
Obfuscated JavaScript code is code that's difficult for humans to understand. Here's an example:
var _0x6405=["\x73\x65\x61\x72\x63\x68","\x65\x78\x65\x63","\x3D","\x28\x2E\x2B\x3F\x29\x28\x26\x7C\x24\x29",""];function getURLParameter(_0xc2bex2){return decodeURI((RegExp(_0xc2bex2+ _0x6405[2]+ _0x6405[3])_0x6405[1]|| [,null])[1]|| _0x6405[4])}The above obfuscated code is actually a really common script that you may use to call-out URL parameters on your landing page:
function getURLParameter(name) {
return decodeURI(
(RegExp(name + '=' + '(.+?)(&|$)').exec(location.search)||[,null])[1] || ''
);
}Many times malicious scripts that steal your traffic are hidden like this.
It can be quite complicated. I'm not going to go into detail about this in this post, but you can Google more information about it.
Check For External URLs Loading
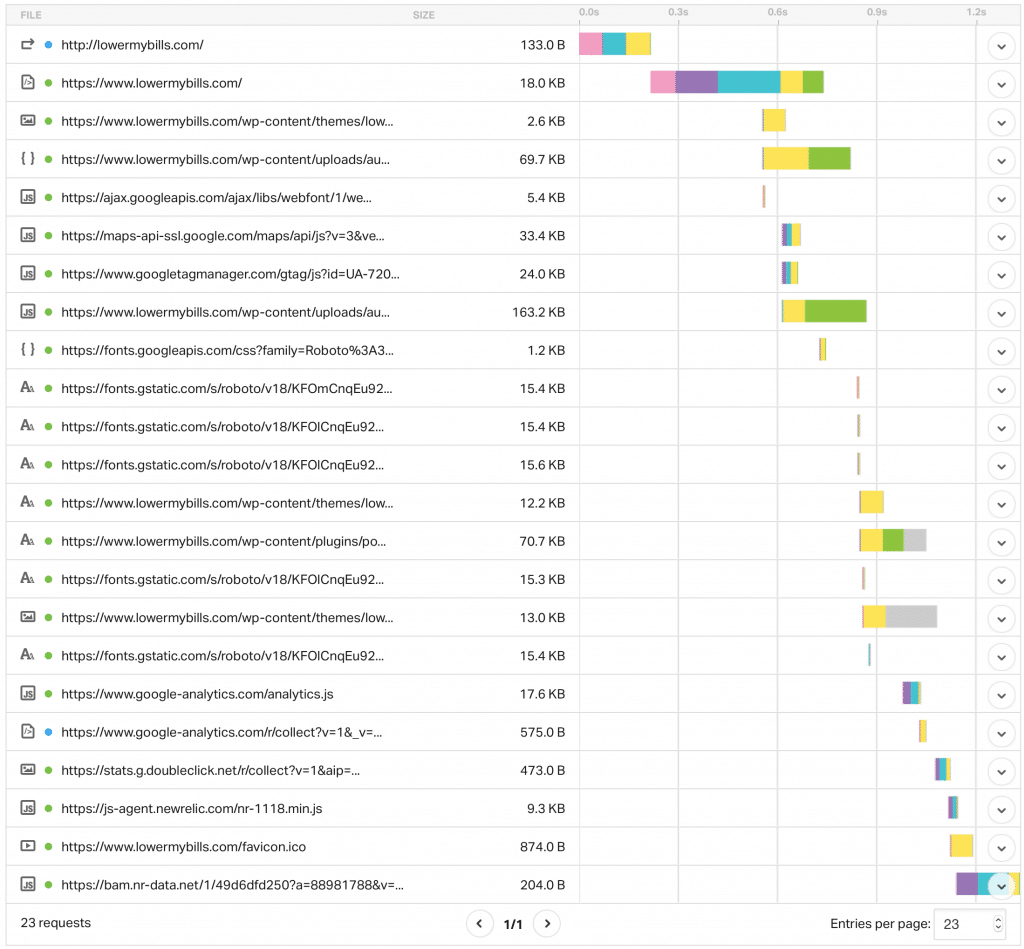
After you've done all the above cleaning, you are going to want to double check that you aren't loading any external files from malicious websites.
You can do this with a tool like Pingdom, or in your browser using the developer tools (network tab in Chrome).
The only external URLs you should load are from official websites, like CDNs, for example.
If In Doubt, Start Over
If you think something malicious could still be happening on the landing page you ripped it's best to just trash it and start over. Or, you could ask someone with more technical knowledge than you to take a look at it.
This will likely cost money, but it'd be worth it if you're going to be spending big money on your campaign.
Final Notes About Cleaning Ripped Landing Pages
This is by no means a complete guide to ripping and cleaning landing pages. There literally thousands of ways to code a landing page and of course every coder does it differently.
It should, however, give you a good idea what to look for and what needs to be changed when you rip a lander. Don't forget to add your own special twist to the page you rip, otherwise, you probably won't make any money!
If this whole process seems over your head, you can also use a CPA landing page builder that allows you to import pages and edit them easily.
